基于X-Pack权限控制版ES,给不同项目组、用户分配不同的权限
创建角色
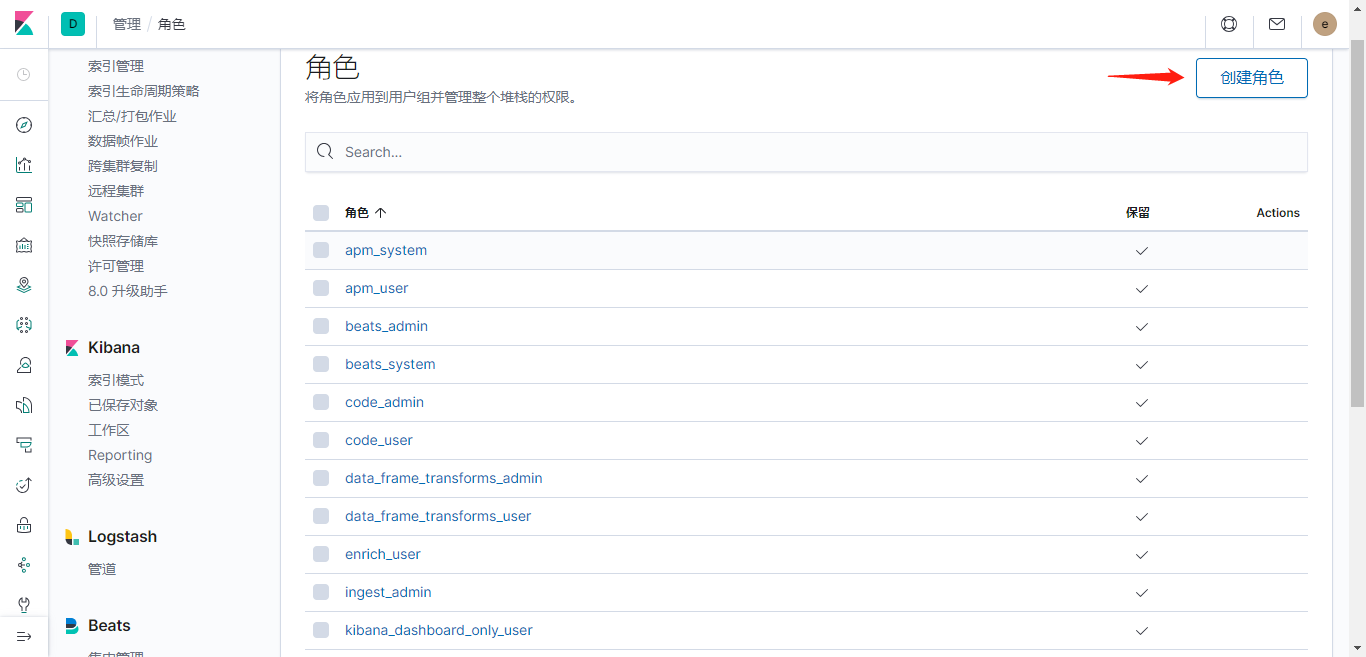
设置角色的ES权限
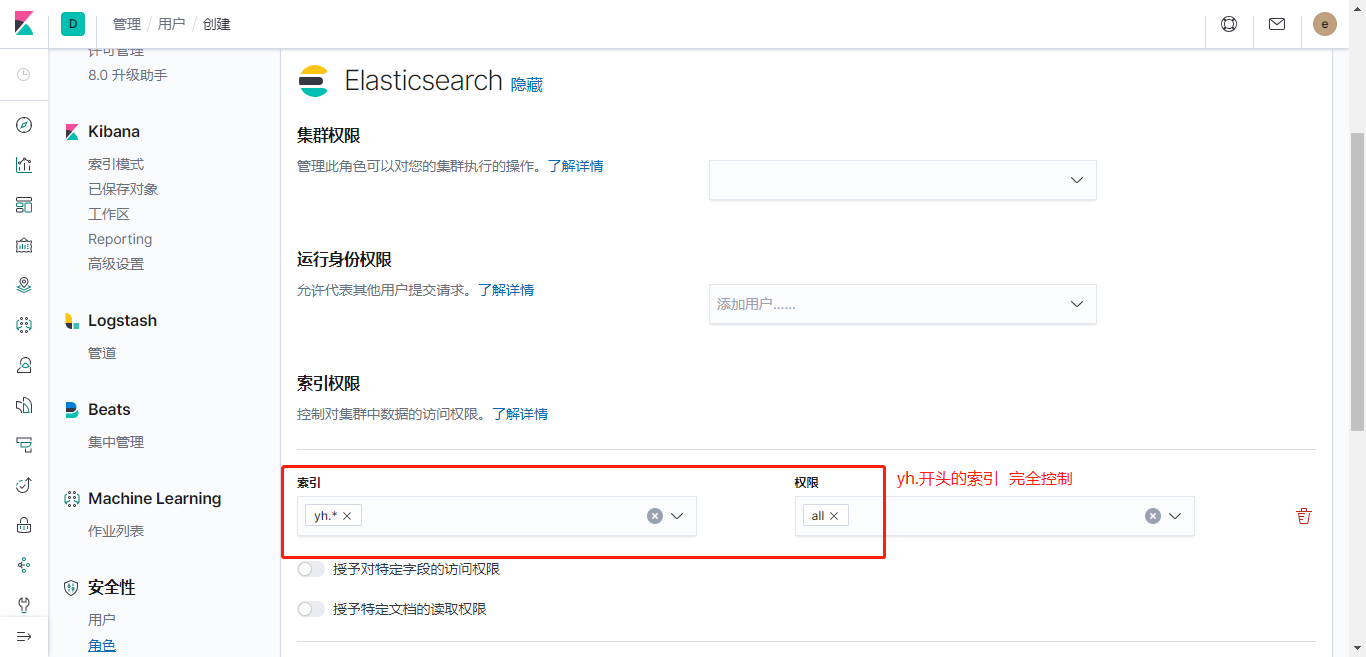
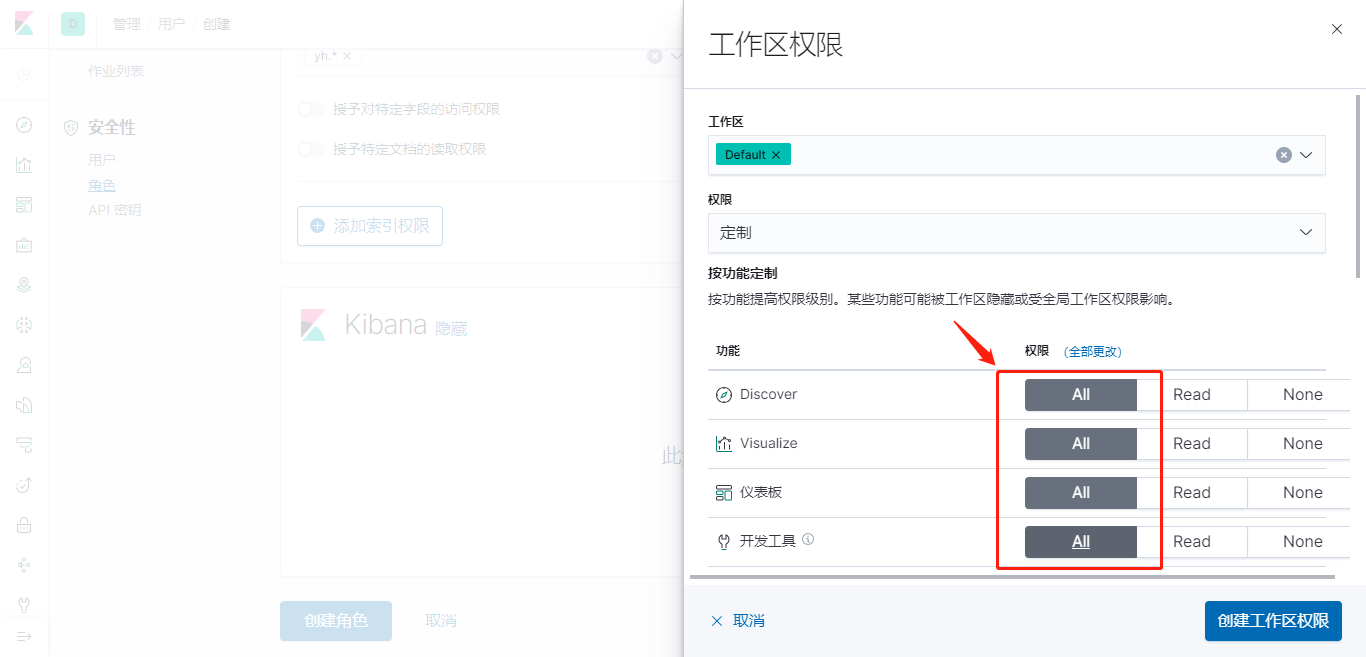
设置角色的Kibana权限
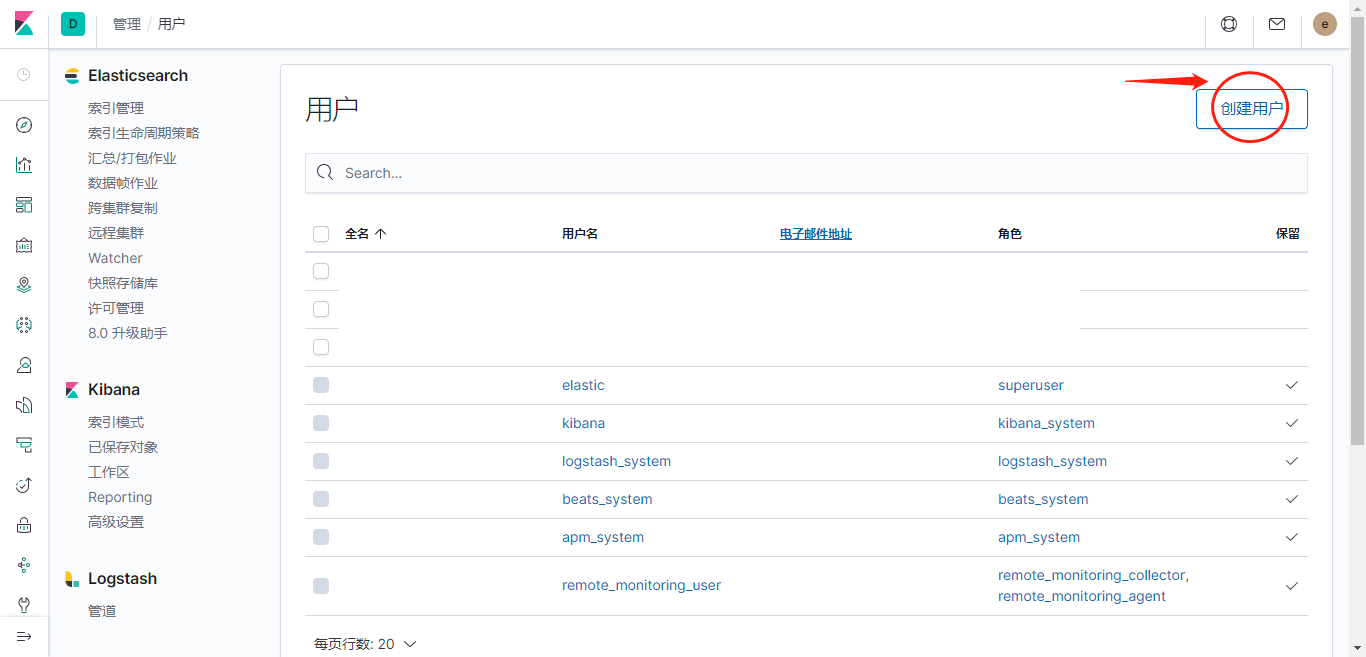
创建用户
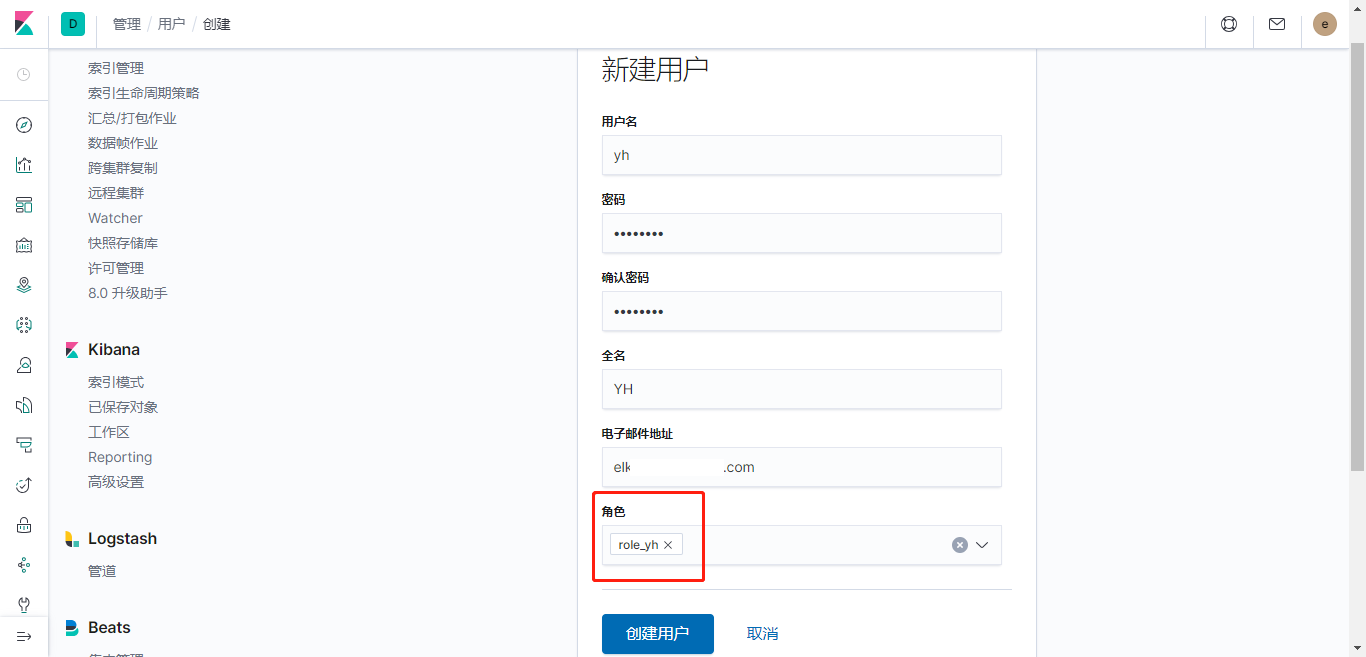
新用户登录
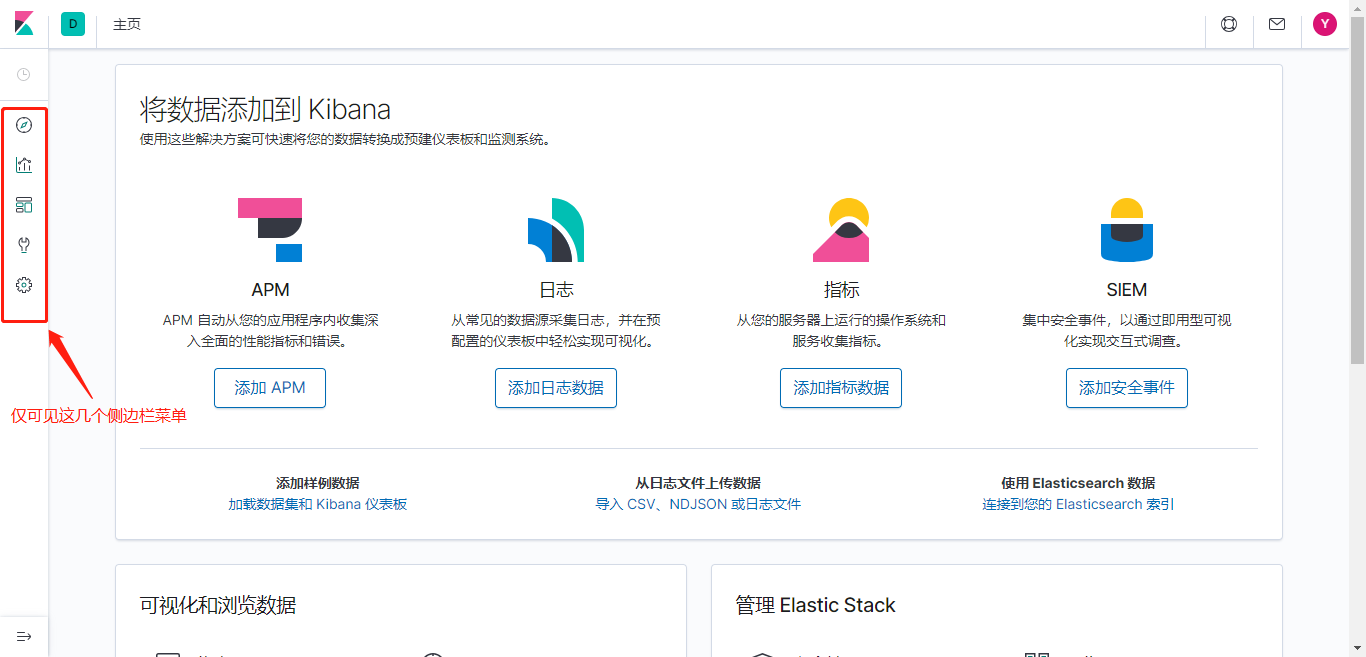
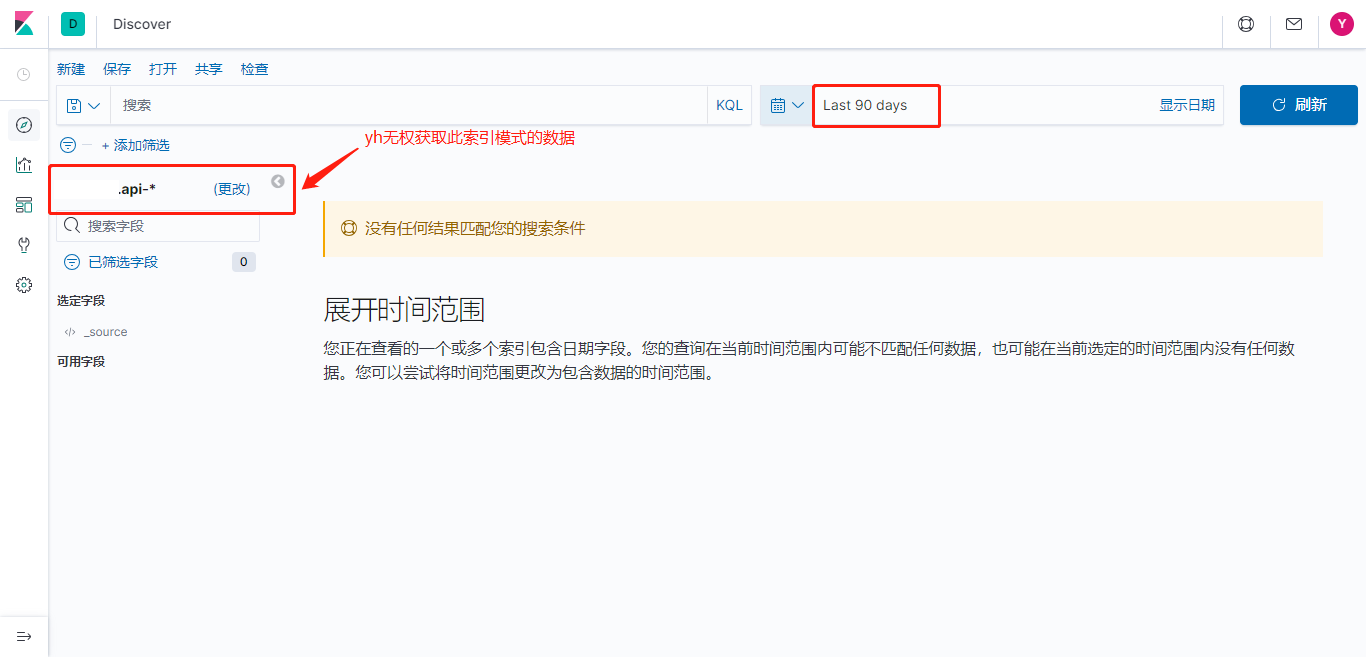
测试ES索引权限
1 | curl -XPUT -u es:password "http://es.keep.com/es-test/_doc/1?pretty" -H 'Content-Type: application/json' -d ' |
1 | { |
权限不够,不能创建该索引。
使用elastic账号查看已创建的role_es具体有哪些权限:
1 | curl -XGET -u elastic:xxxxxx "http://es.keep.com/_xpack/security/role/role_es" |
1 | { |
由于给role_es角色分配的ES索引权限是仅名称以es.开头,故无权创建es-test。改为创建es.test再试则成功:
1 | { |
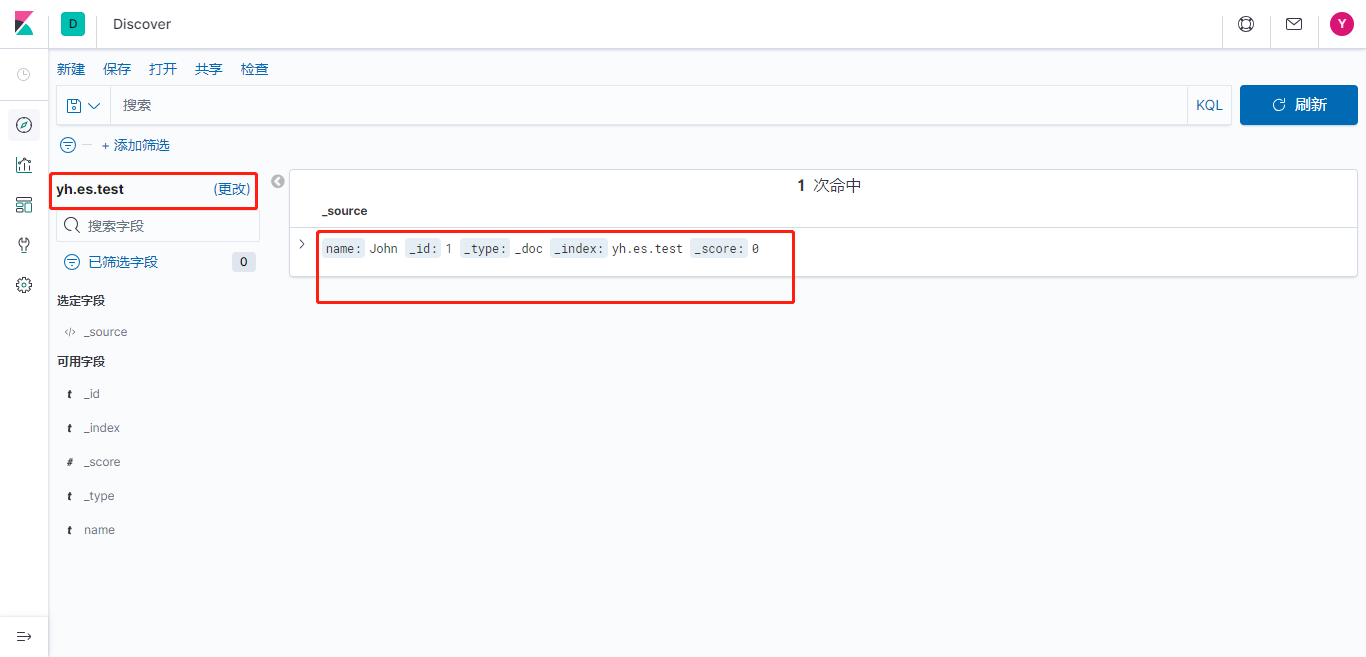
账号规划
根据以上,初步设置了以下账号:
| 角色 | 现有账号 | ES索引权限 | Kibana工作区权限 |
|---|---|---|---|
| role_es | es | es.* | 发现 feature_discover.all 可视化 feature_visualize.all 仪表板 feature_dashboard.all 开发工具 feature_dev_tools.all 索引模式 eature_indexPatterns.all |
| role_k8s | k8s | k8s* | 同上 |