基于X-Pack权限控制版ES,给不同项目组、用户分配不同的权限
创建角色
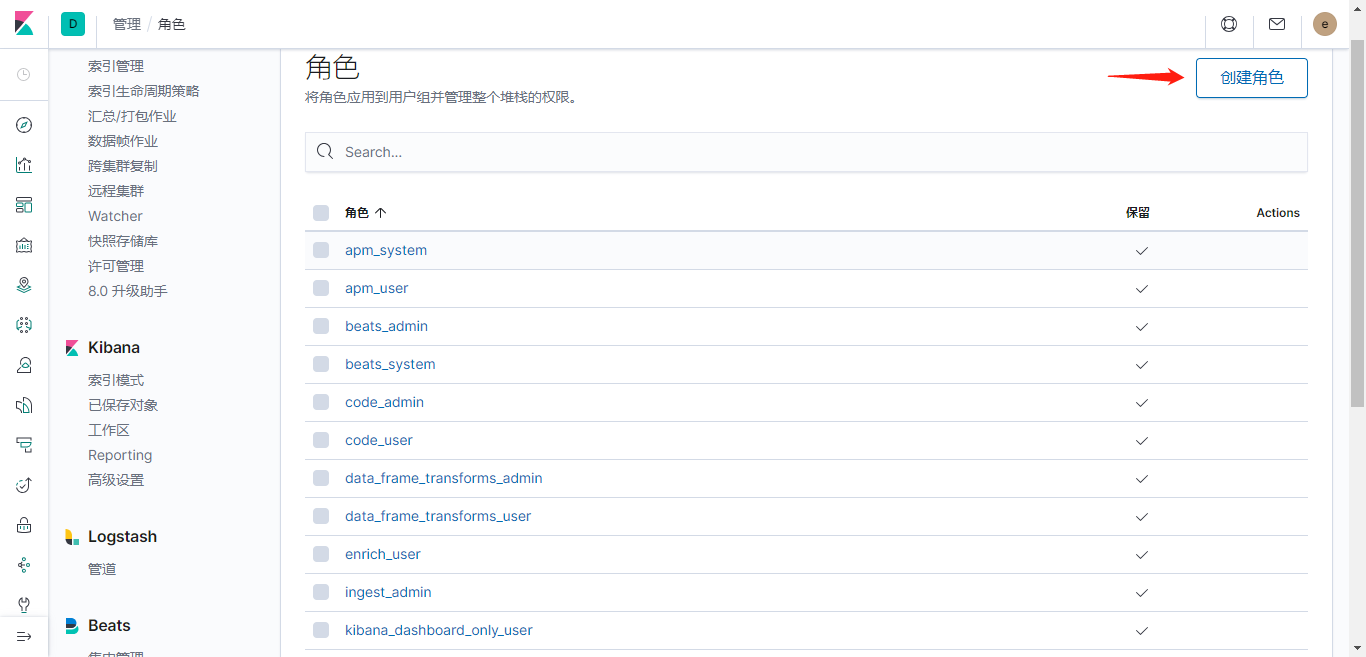
设置角色的ES权限
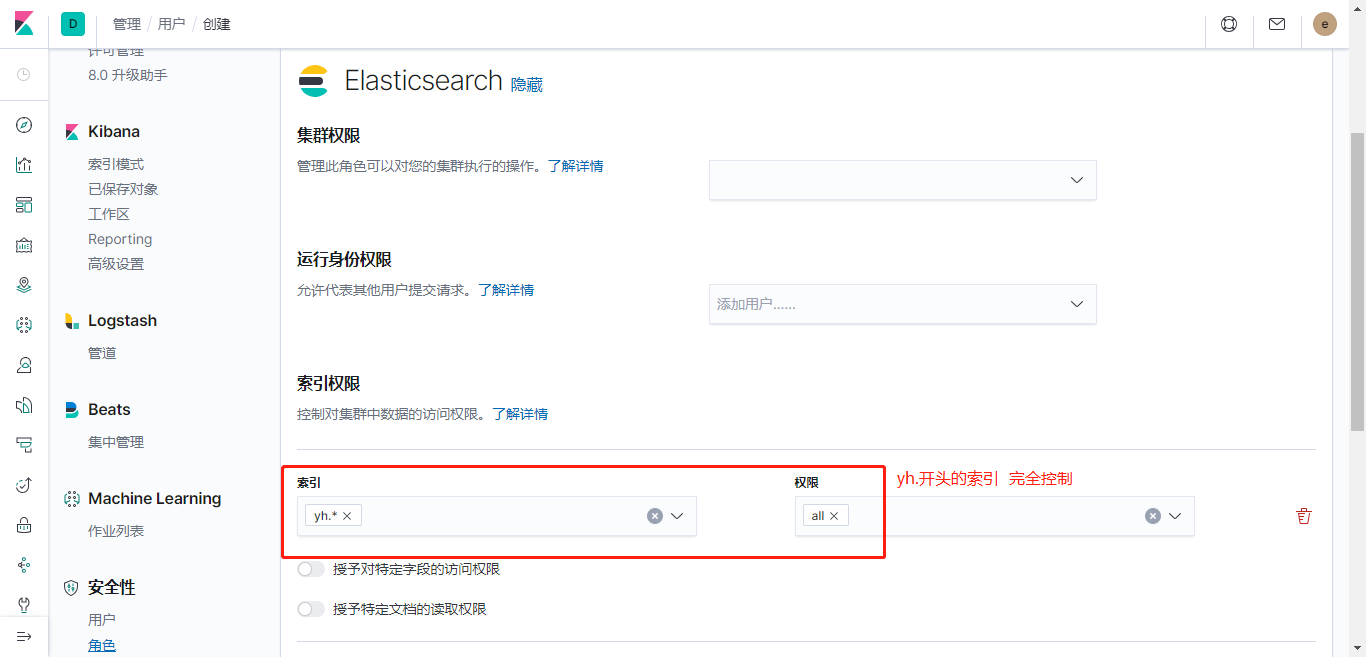
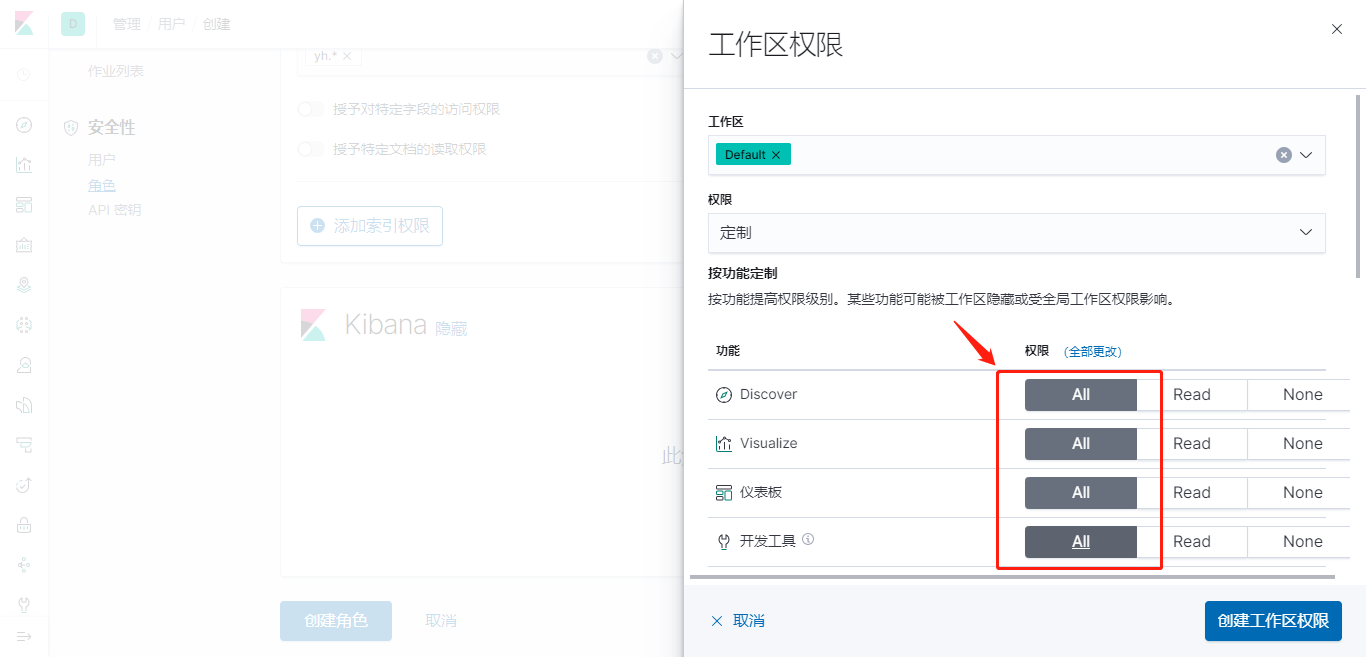
设置角色的Kibana权限
创建用户
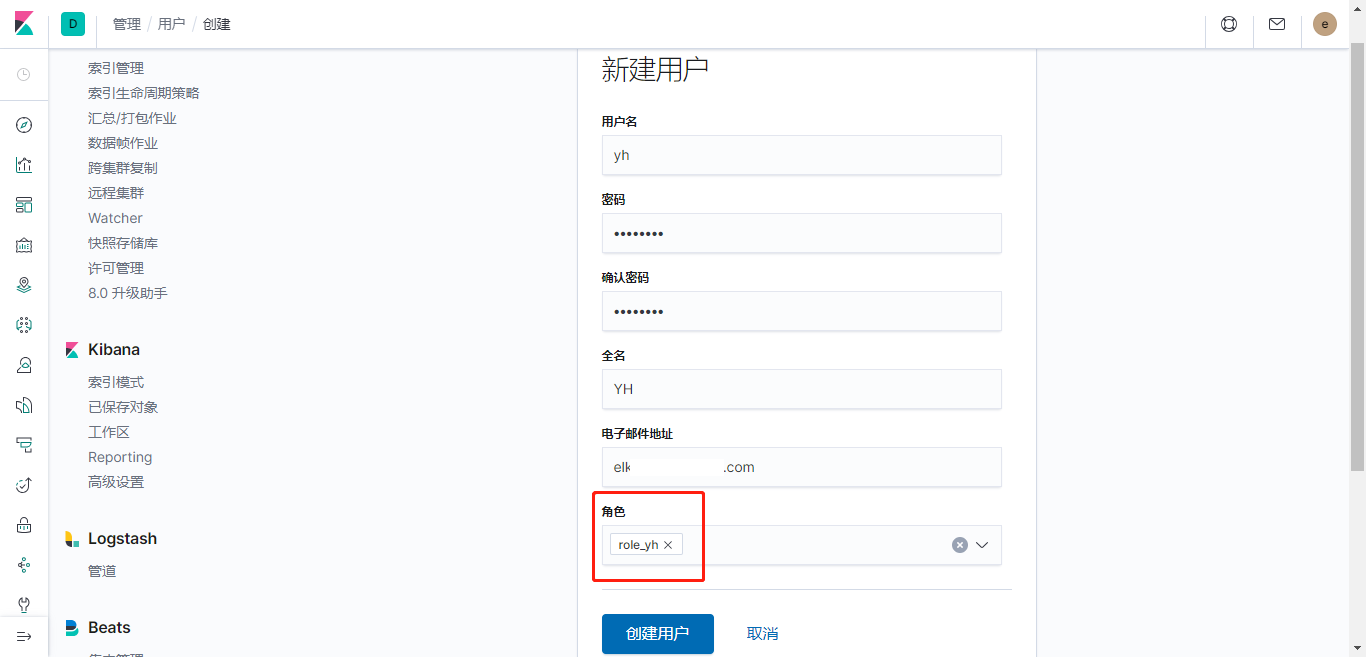
新用户登录
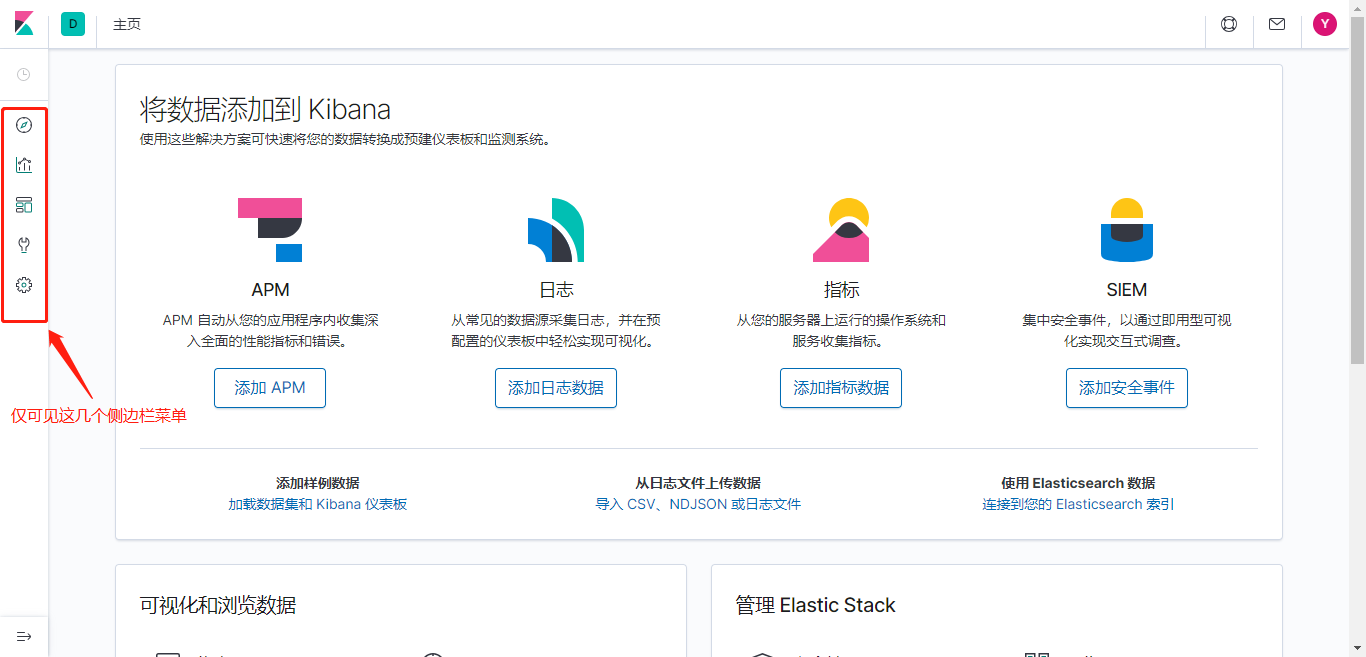
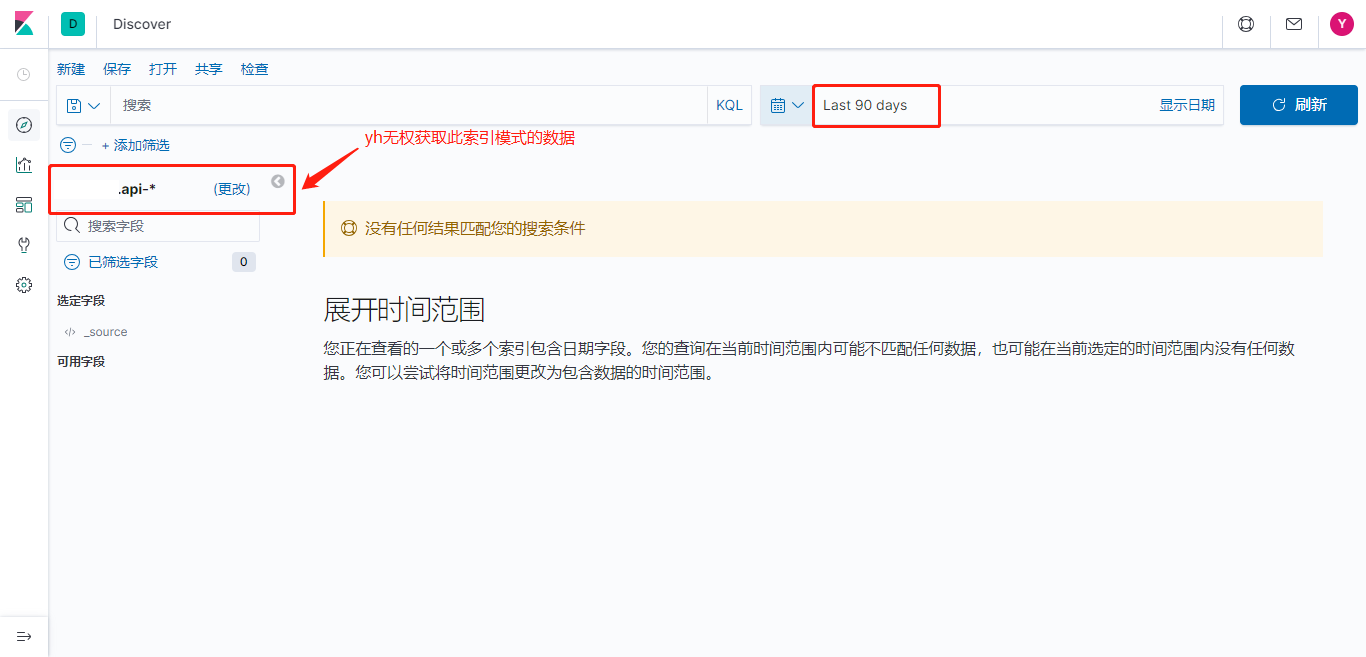
测试ES索引权限
1
2
3
4
| curl -XPUT -u es:password "http://es.keep.com/es-test/_doc/1?pretty" -H 'Content-Type: application/json' -d '
{
"name": "John"
}'
|
1
2
3
4
5
6
7
8
9
10
11
12
13
| {
"error" : {
"root_cause" : [
{
"type" : "security_exception",
"reason" : "action [indices:admin/create] is unauthorized for user [es]"
}
],
"type" : "security_exception",
"reason" : "action [indices:admin/create] is unauthorized for user [es]
},
"status" : 403
}
|
权限不够,不能创建该索引。
使用elastic账号查看已创建的role_es具体有哪些权限:
1
| curl -XGET -u elastic:xxxxxx "http://es.keep.com/_xpack/security/role/role_es"
|
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
| {
"role_es": {
"cluster": [],
"indices": [
{
"names": [
"es.*"
],
"privileges": [
"all"
],
"field_security": {
"grant": [
"*"
],
"except": []
},
"allow_restricted_indices": false
}
],
"applications": [
{
"application": "kibana-.kibana",
"privileges": [
"feature_discover.all",
"feature_visualize.all",
"feature_dashboard.all",
"feature_dev_tools.all",
"feature_indexPatterns.all"
],
"resources": [
"space:default"
]
}
],
"run_as": [],
"metadata": {},
"transient_metadata": {
"enabled": true
}
}
}
|
由于给role_es角色分配的ES索引权限是仅名称以es.开头,故无权创建es-test。改为创建es.test再试则成功:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
| {
"_index" : "es.test",
"_type" : "_doc",
"_id" : "1",
"_version" : 1,
"result" : "created",
"_shards" : {
"total" : 2,
"successful" : 1,
"failed" : 0
},
"_seq_no" : 0,
"_primary_term" : 1
}
|
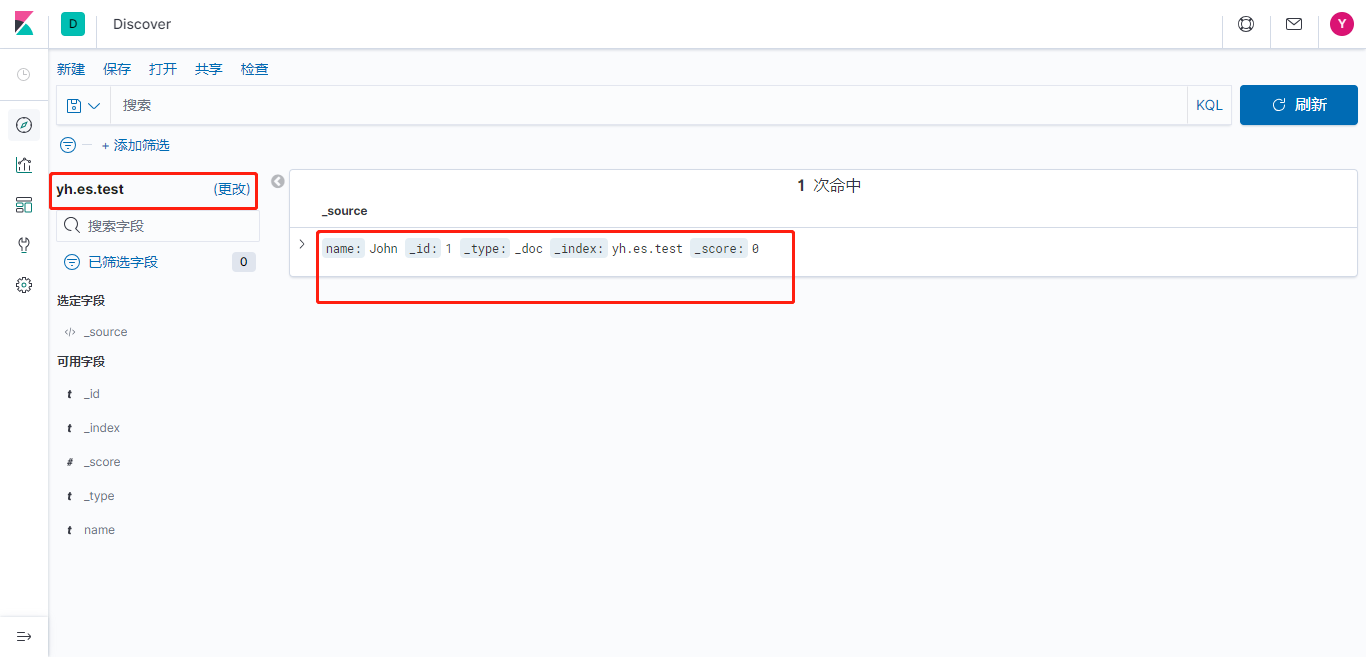
账号规划
根据以上,初步设置了以下账号:
| 角色 |
现有账号 |
ES索引权限 |
Kibana工作区权限 |
| role_es |
es |
es.* |
发现 feature_discover.all
可视化 feature_visualize.all
仪表板 feature_dashboard.all
开发工具 feature_dev_tools.all
索引模式 eature_indexPatterns.all |
| role_k8s |
k8s |
k8s* |
同上 |







